If you are already using the standard security tools like real-time antimalware scanning, installing system updates and provided OS firewall functionalities you might be interested in moving this one step further with dns filtering. DNS (or domain name system) is responsible for translating internet names (like www.google.com) into technical ip addresses used to get the request to the server and the wanted data back. If that returned data is bad, hopefully the antimalware scanner will catch it – but what if we could just redirect the request pointing to malware sites? This is were dns filtering can help – known malicious or unsuitable web addresses will just be answered with a different IP address, so accessing the content provided on the originally provided one is just not possible. This can be used to restrict access to known malware sites or content servers providing additonal downloads for malware tools, but also to restrict access to adult content. If done on DNS level, it will not only affect the web browser, but also everything that is embedded into emails or directly accessed from any application running on your device. In some cases it could also block fresh but uncategorized wanted content, but that’s a really rare occurence. Sounds interesting? Let’s start!
restrictions
I have found a restriction which you might run into: I am on Vodafone for mobile phone in Germany and Vodafone only allows DNS servers based in Germany to resolve the required DNS entries for Wifi Calling. Using DNS servers located outside Germany for filtering or instead of your provider’s DNS servers (Google’s 8.8.8.8 is not your provider’s DNS!) will stop Wifi Calling from working. You have been warned – if you require Wifi Calling to work, changing the DNS servers used might stop this form working.
implementation methods
I am currently aware of two implementation options that you can use on your home network or devices. First one is to change the DNS servers your internet router is pointing to. This protects the complete internal network unless it is overridden directly on the client. As you might want to protect your mobile devices like phones, tablets or notebooks when on the road as well, those can be protected with installing an additional client taking care of redirecting DNS traffic even when used outside your protected home network. The combination of both approaches provides a neat and quite easy setup which will increase your security and protection level with a solution which is used by most of the bigger companies already since years.
some possible solutions for dns filtering
Here’s a short list of some common known solutions for dns filtering that I came across in the past and where applicable I also added some comments on my experience with them so far.
- OpenDNS Family Shield / Home (free) or Home VIP (paid)
- had all already, generally blocks to much and leaves non-english sites still accessible, Home VIP recommended so you can whitelist sites needed
- performance was noticably slower then using the internet provider’s DNS servers
- no mobile clients solution, back when I used it there was no IPv6 support
- OpenDNS Umbrella Prosumer (paid)
- actually this is Cisco Umbrella internet security solution on a 5 user limitation
- also had this for one full year: good features, whitelisting possible, good basic blocking
- mobile protection agents for Windows or macOS clients included, but no mobile phone or tablet protection (at least definitely without having a complete Mobile Device Management at hand and deployed)
- Quad9 (free)
- out of question for me without roaming or mobile OS clients
- NxFilter (free)
- no roaming or mobile OS clients and additionally requires you to run a DNS server on your own
- 1.1.1.1 (free) / Cloudflare Teams ZeroTrust WebSecurityGateway (free up to 50 users)
- that’s what I am currently using – very solid, fast and reliable with good filtering
- clients for Windows and macOS as well as Android or iOS available and you can also reconfigure your internet router with all possible DNS protocols to make that work
- Cloudflare Teams is free up to 50 users and allows you to configure black- and whitelisting on your own, but requires quite a bit more setup work and provides some more options/extensions that might be interesting if you are on the more technical side of things
If you would like to give 1.1.1.1 a try, please continue reading for some additional information and implementation tips.
Router configuration
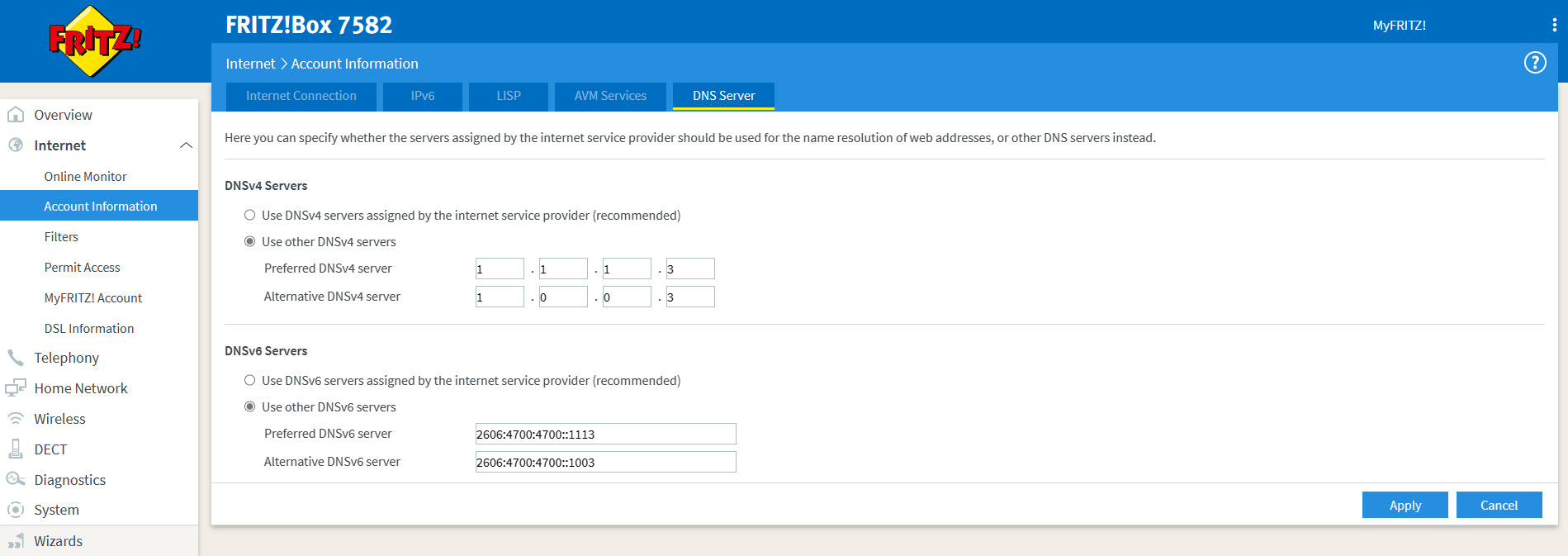
To configure your router open 1.1.1.1 Family and start scrolling down until you can see the two boxes with ‘malware blocking only’ on the left and ‘malware and adult content blocking together’ on the right. Just click one of the appropriate setup instructions link near the bottom of the box and it will take you the information you’ll need for setting up your router. On the FRITZ!Box you can alter the DNS servers used within Internet / Account Information on the tab DNS Server. Depending on your model and firmware, you may also be able to use DNS over HTTPS or DNS over TLS – mine here does not support those new protocols, so I just had to enter the provided IPv4 and IPv6 addresses for their nameservers there and afterwards click on Apply to save the settings.
Test links for checking the setup are provided within the configuration guide as well and those will only work for testing filtering with 1.1.1.1:
Test for 1.1.1.1 malware filtering
Test for 1.1.1.1 adult content and malware filtering
If you tried those links before the implementation was done, you’ll need to wait a while until the DNS cache has been aged out and the request is resend to the DNS, which will retrieve the new redirected IP address target.
WARP Client Configuration
Downloading and installing the client on your notebook or mobile device is fairly straight forward and you just need to follow the instructions for it. At least on iOS you’ll need to implement the VPN tunnel provided by the app as this is the only option to redirect DNS requests there. As I don’t want you to run into certain issues later, here are some things I would like to make you aware of and you will need to take a decision for yourself on each one:
- use WARP for redirecting all web traffic to Cloudflare to get it scanned there
- would improve security at the cost of reduced privacy and at least on mobile devices you have to pay to get your traffic scanned
- will quite sure create issues with latency-sensitive traffic like voice calls, video meetings, gaming or remote control solutions
- mode can be switched on the Windows Client using the gear icon between 1.1.1.1 and 1.1.1.1 with WARP – don’t forget that you need to flick over the main switch to the right to enable protection
- within the WARP client settings on the connections tab you can get your wifi excluded if you did set up the DNS filtering on the router already – if you are using the WARP tunnel, this will switch off the remote traffic scanning as well!
- THIS ONE IS IMPORTANT: on the same tab you need to set your 1.1.1.1 family mode – which curiously is off by default
- on the account tab you can link your devices together – that does not synchronize settings, but if you are using the remote scanning you’ll only need one subscription
- on the same tab you can sign in into Cloudflare Zero Trust if you want to go for the fully-configurable solution
- advanced tab is something you should maybe look into as well – local domain fallback should definitely include your internal domain name provided by your router or you will not be able to resolve internal hostnames in worst case
- you can get that information on Windows when you start a command prompt or powershell and then run ‘ipconfig’ there – look for the connection specific dns suffix shown there
- for a FRITZ!Box it is ‘fritz.box’ and you should add that to that list for sure

